A visual primer to bitcoin vaults
We use the term “bitcoin vault”, or “vault”, to describe a bitcoin wallet that can only be spent via access points. This is NOT the same as the bitcoin vault protocols being proposed by bitcoin covenant proponents; If you don’t know what that is, don’t worry, you don’t need to.
An access point provides a way to view and sign transactions using two or more secrets that reveal the wallet’s master key when combined. Access points allow us to keep our secrets separate allowing for a much more robust security model.
The following diagram illustrates access points that we might design for our bitcoin vault.
This diagram makes use of the ColdCard, XOR Seeds, and BlueWallet’s “Watch-Only wallet”. Your final setup may differ and use alternative tools with different features.
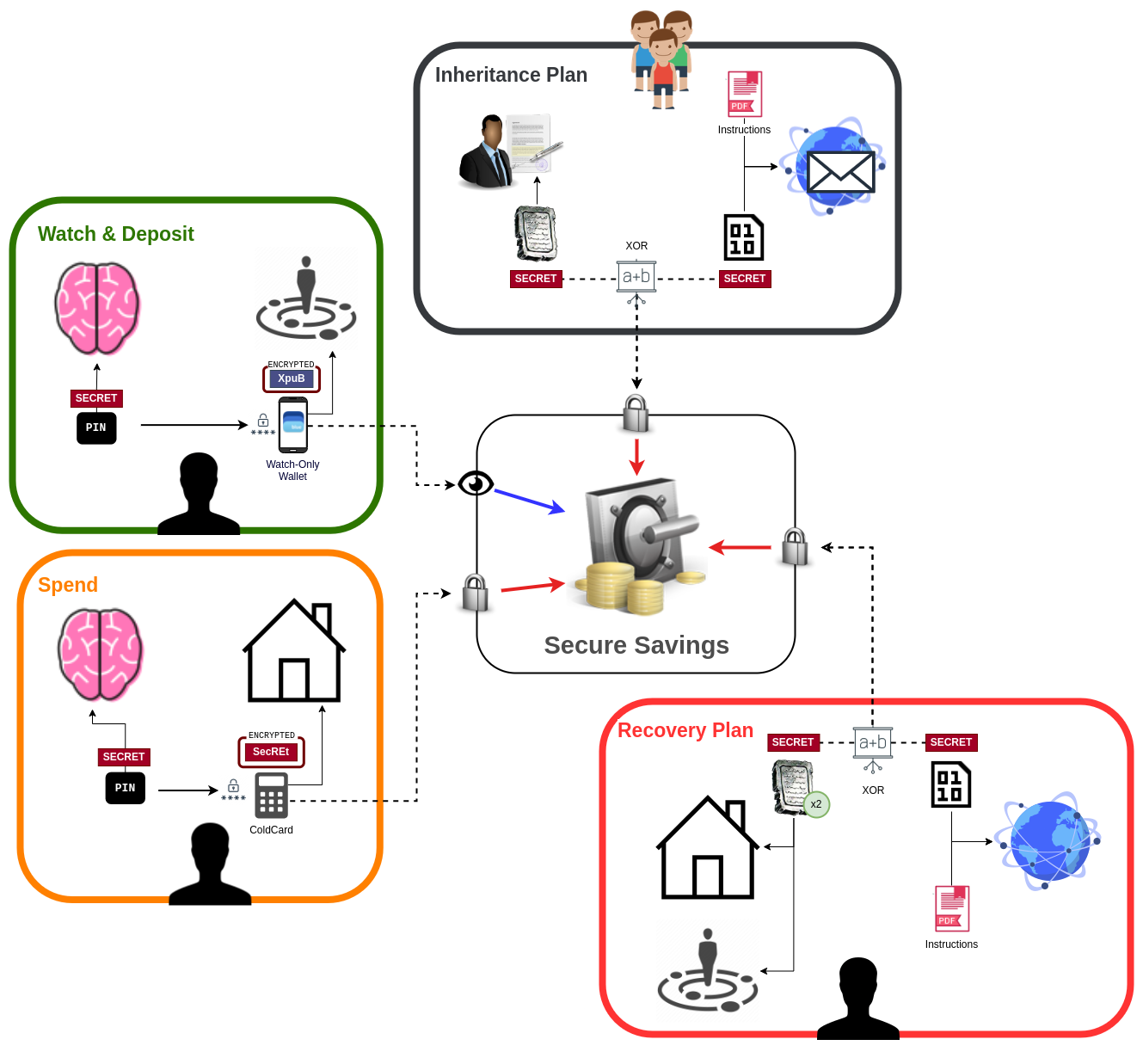
Our theoretical setup has 4 access points:
- A watch and deposit wallet 1
- A spend wallet
- A recovery plan
- An inheritance plan
1 The watch and deposit wallet is read-only; this means that it cannot be used to control our bitcoin, only to observe and track it.
Don’t worry if the diagram above seems overwhelming, the following sections will break down each access point to give you an idea of what they are, and how and why they work.
The watch and deposit wallet
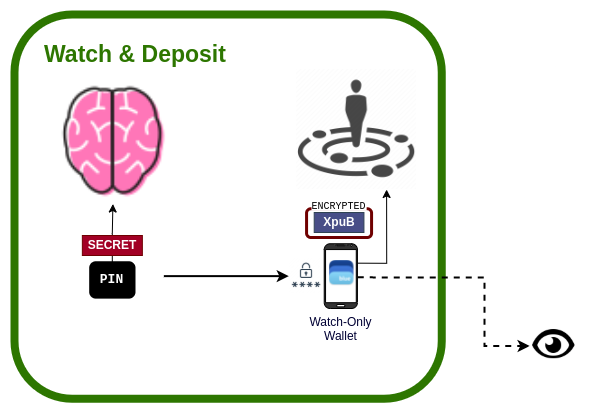
This access point only gives us access to view our wallet. This is the reason for the eye symbol instead of the lock symbol.
This access point of the setup allows us to view our balance and to deposit funds into our vault only. It has the simplest set up of all:
- We keep our pin to ourselves
- We keep our mobile device locked and within close proximity to ourselves
We take advantage of the fact that most modern mobile devices keep our data encrypted when locked. It gives us a convenient way to interact with our bitcoin vault, which will help us resist the urge to compromise our security for convenience by reaching for our hardware wallet unnecessarily.
During setup, we will require a hardware wallet that can export an extended public key (XPUB) to our mobile device. This is a secret that can reveal public addresses, but cannot reveal any private keys and therefore cannot be used to spend any bitcoin. It can, however, sum and display our balance, and it can present unused receive addresses for deposits to our vault.
Bitcoin addresses can be thought of as one-time use banking account details that we often present to others as a QR code. Wallets like BlueWallet make one-time use address management seamless.
It is important to note that this setup is not secure enough for an unrestricted access point. Our mobile device is often connected to the internet, is a general purpose device, and is therefore vulnerable to all the latest malware over time.
The spend wallet
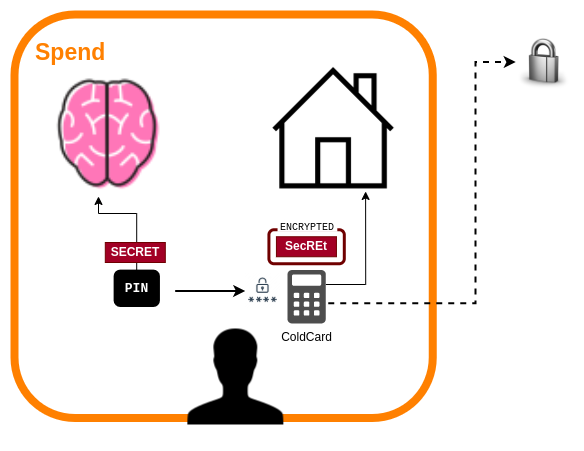
The spend wallet allows us to create and sign transactions from set of bitcoin addresses. We can safely use this with our watch-only wallet since the hardware wallet will never expose its secret to the mobile device or the world wide web.
The security model of this access point relies on a relatively safe home to reduce the chances of losing the hardware wallet device, however the ColdCard provides quite a few security features such as its self destruction after 13 bad pin attempts, and a “brick me pin” that can be left nearby the device as a trap. This can be useful to foil the attempts by a house robber or even a thieving friend or family.
The ability to spend is protected by following main factors:
- we require physical access to the device
- the device is stored safely within a secure home
- we require knowledge of the access pin(s)
- the device is designed to be very difficult to break
- the device holds its secret encrypted on chip
The recovery plan
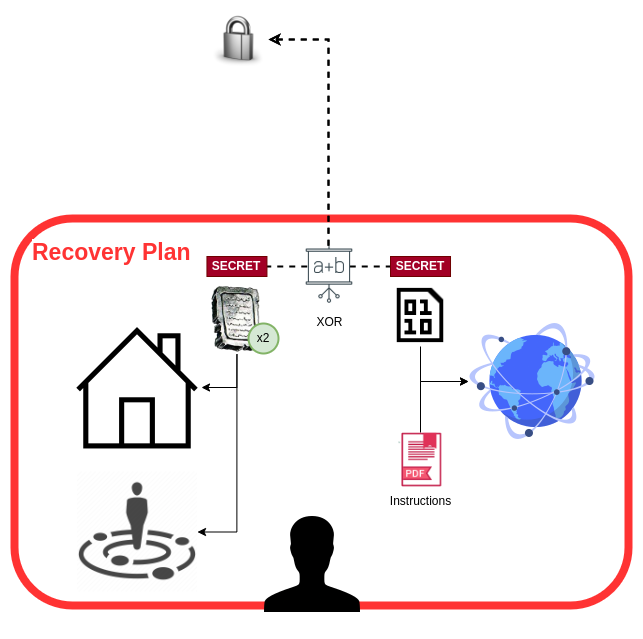
A recovery plan should be considered a one time use tool. If we ever need to use it, it means that our vault is compromised and we should use it to move funds to a new vault as soon as we can create one.
As part of setting up our hardware wallet, we will have a 24 word mnemonic phrase written down which we are expected to hide and protect. This is the most basic form of a recovery plan, but it can also be easy to lose, steal or destroy. It does not qualify for an “access point”, whereas this recovery plan does.
Our recovery plan uses a technique called “Seed XOR” to split our backup into two keys, and store them separately. We will carefully store one key digitally online, and the other on a physical medium.
This setup protects our bitcoin from theft:
- If our digital key is compromised, hackers will not be able to access our bitcoin without the physical counterpart.
- If physical key is stolen, a robber is unlikely to have access to the digital counterpart.
It also protects our bitcoin from losses:
- If stored on a reputable cloud storage such as Dropbox, Google Drive or similar, our digital key will automatically be duplicated which protects it from accidental loss and our cloud account can typically be restored even if we forget our account password.
- Our physical key is duplicated to ensure that we have backup copies if our key is ever lost or stolen, and the requirement of needing the digital counterpart means that creating duplicates will not directly compromise our bitcoin in the way that the basic recovery solution might.
One copy of our physical secret is kept in a secure location such as our home, and the other is kept in close proximity to ourselves. We can create more copies if desired, however none should be in digital form.
Finally, we include a document with detailed instructions that should ease our minds and allow us to calmly and safely recover our bitcoin in a possibly stressful situation.
To recover, we need access to one of the physical keys, and one of the digital keys. We can then either use a new ColdCard or a paper worksheet to combine them for full access to our funds. Of course, the instructional guide will give details about how we plan to sweep the funds.
The inheritance plan
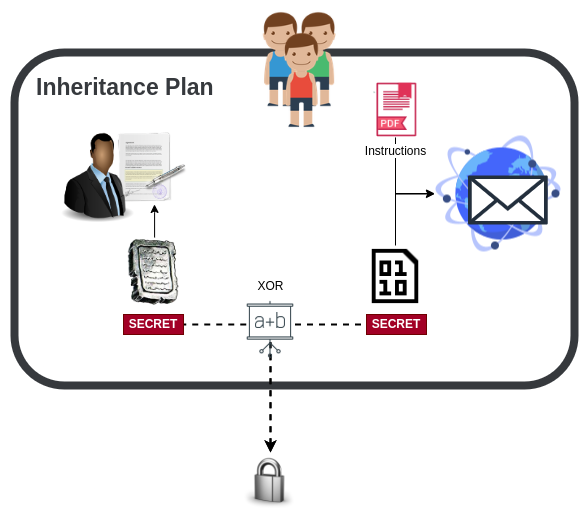
The final access point is the inheritance plan. In our example, we have a physical key that is typically covered, sealed and then given to a trusted lawyer for safe keeping. The second key is given directly to the inheritors, by email along with clear instructions on how to get access and sweep the funds. It should also include links to resources that can be used to educate and/or provide services safely to prevent inheritors from losing money to scams and predatory businesses.
If set up correctly, our lawyer will act as a trigger to provide the missing peices at the right time such that the funds cannot be controlled by anyone but ourselves while we are alive, and only our inheritor(s) will be able to use the funds after our death. We will explore other triggers such as online services and weigh the benefits against the risks and costs.
The recovery plan and the inheritance plan MUST NOT rely on the same keys. Keeping our keys unique across access points ensures that one access plan cannot compromise another. This guide will walk us through creating unique sets of keys safely and correctly.